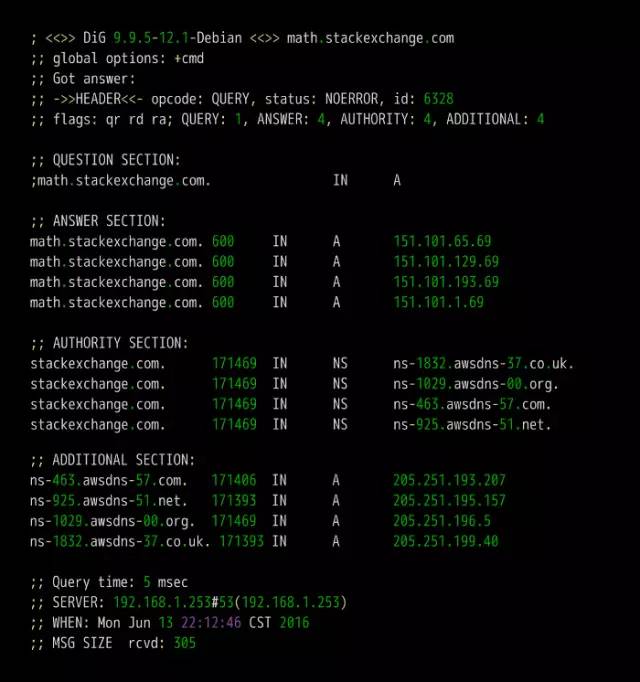
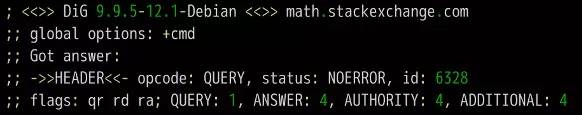
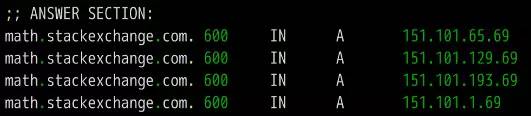
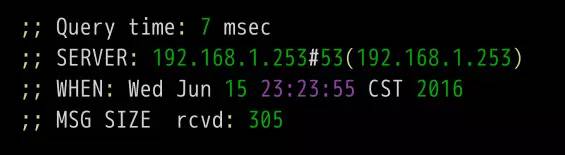
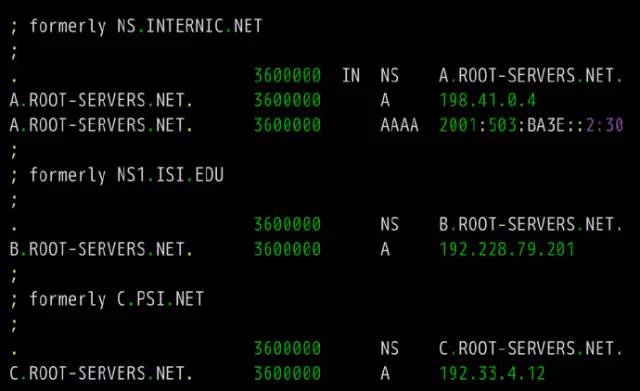
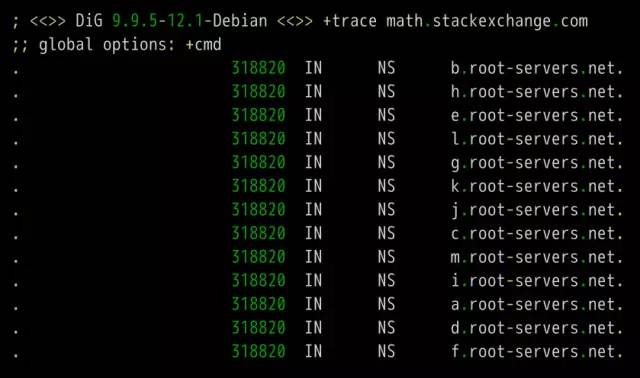
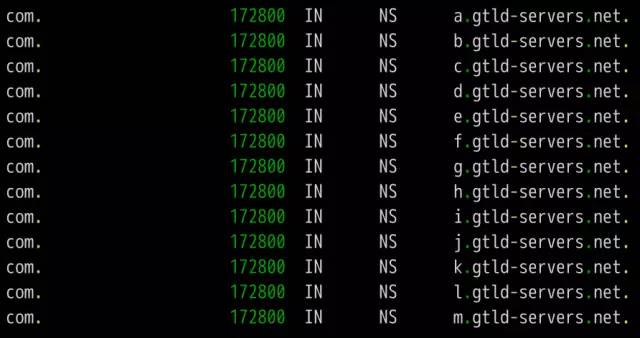
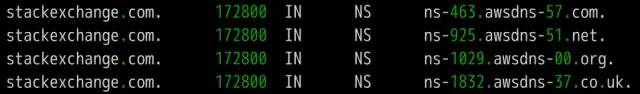
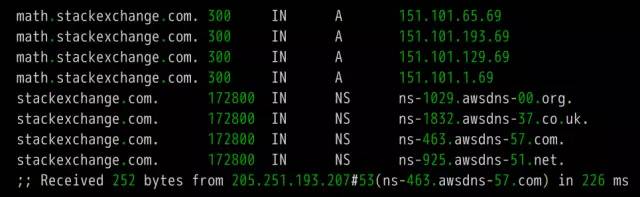
DNS is one of the core protocols of the Internet. Whether it is browsing the Internet or programming, you need to understand its knowledge. What is DNS? The role of DNS (abbreviation of Domain Name System) is very simple. It is based on the domain name to find the IP address. You can think of it as a huge phone book. For example, if you want to access the domain name math.stackexchange.com, you first need to find out through the DNS that its IP address is 151.101.129.69. If you do not know why it is necessary to find out the IP address before you can perform network communication, it is recommended that you read the “Introduction to Internet Protocol†I wrote first. Second, the query process Although only one IP address needs to be returned, the DNS query process is very complicated and divided into multiple steps. Tool software dig can display the entire query process. $ dig math.stackexchange.com The above command will output six pieces of information. The first paragraph is the query parameters and statistics. The second paragraph is the query content. The above result indicates that the A record of the domain name math.stackexchange.com is queried. A is an abbreviation of address. The third paragraph is the reply from the DNS server. The above results show that math.stackexchange.com has four A records, namely four IP addresses. 600 is the TTL value (short for Time to live), indicating the cache time, that is, no re-query within 600 seconds. The fourth paragraph shows the NS records (abbreviation of Name Server) of stackexchange.com, which servers are responsible for managing the DNS records of stackexchange.com. The above results show that stackexchange.com has four NS records, namely four domain name servers. Querying any one of them will tell you what the IP address of math.stackexchange.com is. The fifth paragraph is the IP address of the above four domain name servers. This is returned with the previous paragraph. The sixth paragraph is some of the DNS server's transmission information. The above result shows that the local DNS server is 192.168.1.253, the query port is 53 (the default port of the DNS server), and the response length is 305 bytes. If you do not want to see so much content, you can use the +short parameter. $ dig +short math.stackexchange.com151.101.129.69151.101.65.69151.101.193.69151.101.1.69 The above command only returns 4 IP addresses corresponding to math.stackexchange.com (ie, A records). Third, the DNS server Here we follow the previous example, step by step restore, the machine in the end how to get the IP address of the domain name math.stackexchange.com. First of all, the local machine must know the IP address of the DNS server, otherwise it can't get on the net. Through the DNS server, you can know what the IP address of a domain name is. The IP address of the DNS server may be dynamic. It is assigned by the gateway every time it is used on the Internet. This is called the DHCP mechanism; it may also be a fixed address that is specified in advance. On Linux systems, the IP address of the DNS server is stored in the /etc/resolv.conf file. The DNS server in the previous example is 192.168.1.253, which is an intranet address. There are some public network DNS servers that can also be used. The most famous ones are Google's 8.8.8.8 and Level 3 4.2.2.2. The machine only queries its own DNS server. The dig command has a @ parameter that shows the results of queries to other DNS servers. $ dig @4.2.2.2 math.stackexchange.com The above command specifies to query DNS server 4.2.2.2. Fourth, the domain level How can a DNS server know the IP address of each domain name? The answer is a hierarchical query. Please take a closer look at the previous example. Each domain name has one more dot at the end. For example, the domain name math.stackexchange.com is shown as math.stackexchange.com. This is not negligence. It is the end of all domain names and actually has a root domain name. For example, the real domain name is abbreviated as. Because the root domain name .root is the same for all domain names, it is usually omitted. The next level of the root domain name is called the "top-level domain" (abbreviated as TLD), such as .com, .net; the next level is called "second-level domain" (abbreviated as SLD). For example, in the .example, this domain name can be registered by the user; the next level is the host name, for example, the www inside, also known as the “third-level domain nameâ€, which is the user in their own domain. The name assigned to the server is arbitrarily assigned by the user. To sum up, the hierarchical structure of domain names is as follows. Host name. Subdomain name. Top-level domain name. Root domain name # ie host.sld.tld.root Fifth, the root name server The DNS server performs hierarchical queries based on the domain name hierarchy. What needs to be clear is that each domain name has its own NS record, and the NS records the domain name server that points to that domain name. These servers know the various records of the next-level domain name. The so-called "hierarchical query" is to start from the root domain name, in turn query the NS records of each domain name, until the final IP address is found, the process is roughly as follows. Find the NS record and A record (IP address) of the "top-level domain name server" from the "root name server" Finding "Secondary Domain Name Server" NS Records and A Records (IP Addresses) from "Top Level Domain Name Servers" Check the IP address of the "hostname" from the "secondary domain name server" Looking carefully at the above process, you may find that there is no mention of how the DNS server knows the IP address of the "root name server". The answer is that the NS record and IP address of the "root name server" will not change, so it is built into the DNS server. The following is an example of the built-in root DNS server IP address. The above list lists the three NS records of the root domain (.root) A.ROOT-SERVERS.NET, B.ROOT-SERVERS.NET and C.ROOT-SERVERS.NET, and their IP addresses (ie, A records 198.41.0.4, 192.228.79.201, 192.33.4.12. In addition, it can be seen that the TTL value of all records is 3600000 seconds, which is equivalent to 1000 hours. That is, the list of root name servers is queried once every 1000 hours. At present, there are a total of 13 groups of root name servers in the world, from A.ROOT-SERVERS.NET to M.ROOT-SERVERS.NET. Six, hierarchical query instance The +trace parameter of the dig command can display the entire hierarchical query process for DNS. $ dig +trace math.stackexchange.com The first paragraph of the above command lists all NS records of the root domain name, ie all root name servers. Based on the built-in root DNS server IP address, the DNS server sends a query request to all of these IP addresses and asks the top level domain name server com. NS record for math.stackexchange.com. The first reply to the root domain name server will be cached and will only send requests to this server later. Followed by the second paragraph. The above result shows the 13 NS records of the .com domain name, and also returns the IP address corresponding to each record. The DNS server then issues a query request to these top-level domain name servers and asks the secondary domain name stackexchange.com of math.stackexchange.com for NS records. The above result shows that stackexchange.com has four NS records and returns the IP address corresponding to each NS record. The DNS server then queries the above four NS servers for the host name of math.stackexchange.com. The above results show that math.stackexchange.com has 4 A records, that is, all four IP addresses can access the website. It also shows that the first NS server to return results is ns-463.awsdns-57.com and the IP address is 205.251.193.207. Seven, NS records query The dig command can individually view the NS records for each domain name. $ dig ns com$ dig ns stackexchange.com The +short parameter can show simplified results. $ dig +short ns com$ dig +short ns stackexchange.com Eight, DNS record types The correspondence between domain name and IP is called "record". According to the usage scenario, "records" can be divided into different types. There are already seen A records and NS records. The common DNS record types are as follows. (1) A: Address record, return the IP address pointed to by the domain name. (2) NS: Name server records, returns the server address that stores the next-level domain name information. This record can only be set as a domain name and cannot be set as an IP address. (3) MX: Mail eXchange returns the address of the server that received the e-mail. (4) CNAME: canonical name record (Canonical Name), returning another domain name, ie, the domain name currently queried is a jump of another domain name, as detailed below. (5) PTR: Pointer Record, which is used only for querying domain names from IP addresses. See below for details. In general, in order to ensure the security of the service, there should be at least two NS records, and A records and MX records can also have more than one, thus providing redundancy of services and preventing single point of failure. The CNAME record is mainly used for the internal jump of the domain name, providing flexibility for the server configuration, and the user cannot perceive it. For example, the domain name facebook.github.io is a CNAME record. $ dig facebook.github.io...;; ANSWER SECTION:facebook.github.io. 3370 IN CNAME github.map.fastly.net.github.map.fastly.net. 600 IN A 103.245.222.133 The above result shows that the CNAME record of facebook.github.io points to github.map.fastly.net. In other words, when the user queries facebook.github.io, it actually returns the IP address of github.map.fastly.net. The advantage of this is that when changing the IP address of the server, it is sufficient to modify the domain name github.map.fastly.net. The user's facebook.github.io domain name does not need to be modified. Since the CNAME record is a replacement, once the domain name has set the CNAME record, it can no longer set up other records (such as A records and MX records). This is to prevent conflicts. For example, foo.com points to bar.com, and both domains have their own MX records. If they are inconsistent, problems will arise. Because TLDs usually set MX records, users are generally not allowed to set CNAME records for TLDs. The PTR record is used to check the domain name from the IP address. The -x parameter of the dig command is used to query PTR records. $ dig -x 192.30.252.153...;; ANSWER SECTION: 153.252.30.192.in-addr.arpa. 3600 IN PTR pages.github.com. The above result shows that the domain name of 192.30.252.153 server is pages.github.com. One application of the reverse lookup is to prevent spam, that is, to verify the IP address of the sending email, and whether it really has the domain name it claims. The dig command can view the specified record type. $ dig a github.com$ dig ns github.com$ dig mx github.com Nine other DNS tools In addition to dig, there are some other gadgets that can be used. (1) host command The host command can be thought of as a simplified version of the dig command, returning various records of the current requested domain name. $ host github.comgithub.com has address 192.30.252.121github.com mail is handled by 5 ALT2.ASPMX.L.GOOGLE.COM.github.com mail is handled by 10 ALT4.ASPMX.L.GOOGLE.COM.github. Com mail is handled by 10 ALT3.ASPMX.L.GOOGLE.COM.github.com mail is handled by 5 ALT1.ASPMX.L.GOOGLE.COM.github.com mail is handled by 1 ASPMX.L.GOOGLE.COM. $ host facebook.github.comfacebook.github.com is an alias for github.map.fastly.net.github.map.fastly.net has address 103.245.222.133 The host command can also be used for reverse lookup, ie querying the domain name from the IP address, which is equivalent to dig -x. $ host 192.30.252.153153.252.30.192.in-addr.arpa domain name pointer pages.github.com. (2) nslookup command The nslookup command is used to interactively query domain records. $ nslookup> facebook.github.ioServer: 192.168.1.253Address: 192.168.1.253#53Non-authoritative answer: facebook.github.io canonical name = github.map.fastly.net.Name: github.map.fastly.netAddress: 103.245 .222.133 > (3) whois command The whois command is used to view the registration of a domain name. $ whois github.com Ten, reference link DNS: The Good Parts, by Pete Keen DNS 101, by Mark McDonnell Attached, DNS Encyclopedia, Filterable DNS (Domain Name System) is a distributed database that maps domain names and IP addresses to each other on the Internet. It enables users to access the Internet more conveniently without having to memorize IP strings that can be directly read by the machine. The process of obtaining the IP address corresponding to the host name through the host name is called domain name resolution (or host name resolution). The DNS protocol runs on the UDP protocol using port number 53. In the RFC document, RFC 2181 has a specification for DNS. RFC 2136 describes the dynamic update of DNS. RFC 2308 describes the reverse cache of DNS query. DNS function Each IP address can have a host name. The host name consists of one or more strings separated by a decimal point. With the host name, do not remember the IP address of each IP device. Just remember the relatively intuitive and meaningful host name. This is what the DNS protocol needs to accomplish. There are two ways to map hostnames to IP addresses: 1) Static mapping. Each device is configured with a host-to-IP address mapping. Each device independently maintains its own mapping table and is only used by the device. 2) Dynamic mapping, set up a set of domain name resolution system (DNS), configure host-to-IP address mapping on a dedicated DNS server, the network needs to use the host name communication device, first need to query the host corresponding to the DNS server IP address. The process of obtaining the IP address corresponding to the host name through the host name is called domain name resolution (or host name resolution). When resolving a domain name, static domain name resolution can be used first. If static domain name resolution is not successful, dynamic domain name resolution is used. You can put some commonly used domain names in the static domain name resolution table, which can greatly improve the efficiency of domain name resolution. DNS server The DNS service is provided by a computer that has DNS server software installed. The server software can be based on the linux-like operating system, or it can be based on the Windows operating system. After installing the DNS server software, you can create a zone file in the location you specified. The zone file is a file containing the name of the domain to the IP address resolution record, such as the contents of the file may be: primary name Server = dns2 (the host name of the master server is) Serial = 2913 (serial number = 2913, this serial number is used to copy the file when the secondary domain name server to copy the file) Refresh = 10800 (3 hours) (refresh = 10800 seconds, the secondary domain name server queries a primary server every 3 hours) Retry = 3600 (1 hour) (Retry = 3600 seconds, when the secondary domain name service tries to query for updates on the primary server and the connection fails, the secondary domain name server accesses the primary domain name server every hour) Expire = 604800 (7 days) (Expiration = 604,800 seconds. The secondary domain name server deletes the record in 7 days after the primary service fails to update.) Default TTL = 3600 (1 hour) (The default lifetime = 3600 seconds, the cache server saves the record for 1 hour. That is to tell the cache server to save the domain's resolution record is 1 hour) DNS security issues 1. Malicious attacks against the domain name system: DDOS attack caused domain name resolution. 2. Domain Name Hijacking: Modify registration information and hijack analytical results. 3. State-owned domain name system security incidents: Change of domain name management rights for ".ly" and ".af" domain names. 4. There is a loophole in the DNS service running on the system, which leads to hackers gaining permission to tamper with the DNS information. 5. Incorrect DNS settings result in the leakage of sensitive information. Provides hackers with further information to provide powerful information.
The sound quality of small speakers is also good. It does not have the same large speakers and power as HIFI speakers, and its sound quality cannot compete with large speakers due to physical limitations. But for the vast majority of users who are not golden ears, the use of small speakers with tablets and mobile phones is sufficient to meet their hearing needs.
Wireless Retro Speaker,Waterproof Retro Speaker,Portable Vintage Speaker,Rechargeable Vintage Speaker Shenzhen Focras Technology Co.,Ltd , https://www.focras.com


For Bluetooth speakers, I personally think that when many people buy speakers, the appearance is the first priority and the function is second.
We focus on retro Bluetooth speakers,It has high energy density, mini size, light weight and diversified shapes;Excellent fast charging performance, support fast charging and other excellent features
with a brand-new design, showing retro nostalgia without losing fashion. It uses a 2.5-inch speaker and has many functions such as FM radio, Bluetooth fast connection, multi-mode switching, and HIFI high fidelity. Wireless Bluetooth 4-10 hours of playback (at 50% volume), which adds to its unique charm.